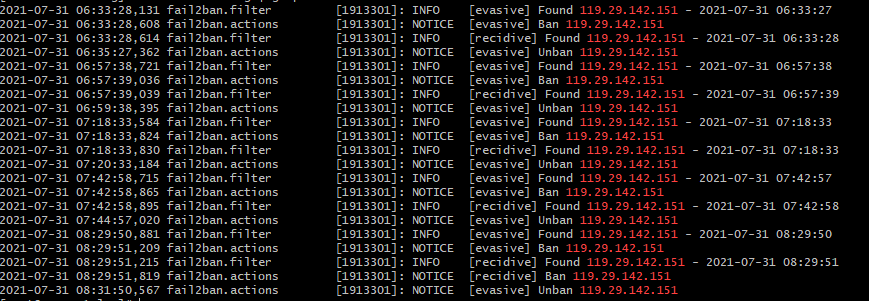
I’m digging into my logs now. A bot is continuously getting requests through in this way using 301 redirects from the “www”:
An occasional 403 pops up, but the users requests seem to be flowing through without any issue.
119.45.240.155 www.domain.org - [02/Aug/2021:17:05:51 -0500] "POST /xmlrpc.php HTTP/1.1" 301 - "-" "Apache-HttpClient/4.5.2 (Java/1.8.0_151)"
119.45.240.155 www.domain.org - [02/Aug/2021:17:05:23 -0500] "POST /xmlrpc.php HTTP/1.1" 301 - "-" "Apache-HttpClient/4.5.2 (Java/1.8.0_151)"
119.45.240.155 www.domain.org - [02/Aug/2021:17:05:23 -0500] "POST /xmlrpc.php HTTP/1.1" 301 - "-" "Apache-HttpClient/4.5.2 (Java/1.8.0_151)"
119.45.240.155 www.domain.org - [02/Aug/2021:17:05:24 -0500] "POST /xmlrpc.php HTTP/1.1" 301 - "-" "Apache-HttpClient/4.5.2 (Java/1.8.0_151)"
119.45.240.155 www.domain.org - [02/Aug/2021:17:05:24 -0500] "POST /xmlrpc.php HTTP/1.1" 403 199 "-" "Apache-HttpClient/4.5.2 (Java/1.8.0_151)"
119.45.240.155 www.domain.org - [02/Aug/2021:17:05:27 -0500] "POST /xmlrpc.php HTTP/1.1" 301 - "-" "Apache-HttpClient/4.5.2 (Java/1.8.0_151)"
119.45.240.155 www.domain.org - [02/Aug/2021:17:05:39 -0500] "POST /xmlrpc.php HTTP/1.1" 301 - "-" "Apache-HttpClient/4.5.2 (Java/1.8.0_151)"
119.45.240.155 www.domain.org - [02/Aug/2021:17:05:40 -0500] "POST /xmlrpc.php HTTP/1.1" 301 - "-" "Apache-HttpClient/4.5.2 (Java/1.8.0_151)"
119.45.240.155 www.domain.org - [02/Aug/2021:17:05:41 -0500] "POST /xmlrpc.php HTTP/1.1" 301 - "-" "Apache-HttpClient/4.5.2 (Java/1.8.0_151)"
119.45.240.155 www.domain.org - [02/Aug/2021:17:05:44 -0500] "POST /xmlrpc.php HTTP/1.1" 301 - "-" "Apache-HttpClient/4.5.2 (Java/1.8.0_151)"
119.45.240.155 www.domain.org - [02/Aug/2021:17:05:46 -0500] "POST /xmlrpc.php HTTP/1.1" 301 - "-" "Apache-HttpClient/4.5.2 (Java/1.8.0_151)"
119.45.240.155 www.domain.org - [02/Aug/2021:17:05:49 -0500] "POST /xmlrpc.php HTTP/1.1" 301 - "-" "Apache-HttpClient/4.5.2 (Java/1.8.0_151)"
119.45.240.155 www.domain.org - [02/Aug/2021:17:05:52 -0500] "POST /xmlrpc.php HTTP/1.1" 301 - "-" "Apache-HttpClient/4.5.2 (Java/1.8.0_151)"
119.45.240.155 www.domain.org - [02/Aug/2021:17:05:53 -0500] "POST /xmlrpc.php HTTP/1.1" 301 - "-" "Apache-HttpClient/4.5.2 (Java/1.8.0_151)"
119.45.240.155 www.domain.org - [02/Aug/2021:17:05:53 -0500] "POST /xmlrpc.php HTTP/1.1" 301 - "-" "Apache-HttpClient/4.5.2 (Java/1.8.0_151)"
119.45.240.155 www.domain.org - [02/Aug/2021:17:05:54 -0500] "POST /xmlrpc.php HTTP/1.1" 301 - "-" "Apache-HttpClient/4.5.2 (Java/1.8.0_151)"
119.45.240.155 www.domain.org - [02/Aug/2021:17:06:01 -0500] "POST /xmlrpc.php HTTP/1.1" 301 - "-" "Apache-HttpClient/4.5.2 (Java/1.8.0_151)"
119.45.240.155 www.domain.org - [02/Aug/2021:17:06:06 -0500] "POST /xmlrpc.php HTTP/1.1" 301 - "-" "Apache-HttpClient/4.5.2 (Java/1.8.0_151)"
119.45.240.155 www.domain.org - [02/Aug/2021:17:06:07 -0500] "POST /xmlrpc.php HTTP/1.1" 301 - "-" "Apache-HttpClient/4.5.2 (Java/1.8.0_151)"
119.45.240.155 www.domain.org - [02/Aug/2021:17:06:11 -0500] "POST /xmlrpc.php HTTP/1.1" 301 - "-" "Apache-HttpClient/4.5.2 (Java/1.8.0_151)"
119.45.240.155 www.domain.org - [02/Aug/2021:17:06:12 -0500] "POST /xmlrpc.php HTTP/1.1" 301 - "-" "Apache-HttpClient/4.5.2 (Java/1.8.0_151)"
119.45.240.155 www.domain.org - [02/Aug/2021:17:06:13 -0500] "POST /xmlrpc.php HTTP/1.1" 301 - "-" "Apache-HttpClient/4.5.2 (Java/1.8.0_151)"
119.45.240.155 www.domain.org - [02/Aug/2021:17:06:15 -0500] "POST /xmlrpc.php HTTP/1.1" 301 - "-" "Apache-HttpClient/4.5.2 (Java/1.8.0_151)"
119.45.240.155 www.domain.org - [02/Aug/2021:17:06:18 -0500] "POST /xmlrpc.php HTTP/1.1" 301 - "-" "Apache-HttpClient/4.5.2 (Java/1.8.0_151)"
119.45.240.155 www.domain.org - [02/Aug/2021:17:06:26 -0500] "POST /xmlrpc.php HTTP/1.1" 301 - "-" "Apache-HttpClient/4.5.2 (Java/1.8.0_151)"
119.45.240.155 www.domain.org - [02/Aug/2021:17:06:27 -0500] "POST /xmlrpc.php HTTP/1.1" 301 - "-" "Apache-HttpClient/4.5.2 (Java/1.8.0_151)"
119.45.240.155 www.domain.org - [02/Aug/2021:17:03:19 -0500] "POST /xmlrpc.php HTTP/1.1" 301 - "-" "Apache-HttpClient/4.5.2 (Java/1.8.0_151)"
119.45.240.155 www.domain.org - [02/Aug/2021:17:03:21 -0500] "POST /xmlrpc.php HTTP/1.1" 301 - "-" "Apache-HttpClient/4.5.2 (Java/1.8.0_151)"
119.45.240.155 www.domain.org - [02/Aug/2021:17:03:22 -0500] "POST /xmlrpc.php HTTP/1.1" 301 - "-" "Apache-HttpClient/4.5.2 (Java/1.8.0_151)"
119.45.240.155 www.domain.org - [02/Aug/2021:17:03:25 -0500] "POST /xmlrpc.php HTTP/1.1" 301 - "-" "Apache-HttpClient/4.5.2 (Java/1.8.0_151)"
119.45.240.155 www.domain.org - [02/Aug/2021:17:03:27 -0500] "POST /xmlrpc.php HTTP/1.1" 301 - "-" "Apache-HttpClient/4.5.2 (Java/1.8.0_151)"
119.45.240.155 www.domain.org - [02/Aug/2021:17:03:28 -0500] "POST /xmlrpc.php HTTP/1.1" 301 - "-" "Apache-HttpClient/4.5.2 (Java/1.8.0_151)"
119.45.240.155 www.domain.org - [02/Aug/2021:17:03:38 -0500] "POST /xmlrpc.php HTTP/1.1" 301 - "-" "Apache-HttpClient/4.5.2 (Java/1.8.0_151)"
119.45.240.155 www.domain.org - [02/Aug/2021:17:03:55 -0500] "POST /xmlrpc.php HTTP/1.1" 301 - "-" "Apache-HttpClient/4.5.2 (Java/1.8.0_151)"
119.45.240.155 www.domain.org - [02/Aug/2021:17:03:56 -0500] "POST /xmlrpc.php HTTP/1.1" 301 - "-" "Apache-HttpClient/4.5.2 (Java/1.8.0_151)"
119.45.240.155 www.domain.org - [02/Aug/2021:17:03:58 -0500] "POST /xmlrpc.php HTTP/1.1" 301 - "-" "Apache-HttpClient/4.5.2 (Java/1.8.0_151)"
119.45.240.155 www.domain.org - [02/Aug/2021:17:04:00 -0500] "POST /xmlrpc.php HTTP/1.1" 301 - "-" "Apache-HttpClient/4.5.2 (Java/1.8.0_151)"
119.45.240.155 www.domain.org - [02/Aug/2021:17:04:00 -0500] "POST /xmlrpc.php HTTP/1.1" 301 - "-" "Apache-HttpClient/4.5.2 (Java/1.8.0_151)"
119.45.240.155 www.domain.org - [02/Aug/2021:17:04:02 -0500] "POST /xmlrpc.php HTTP/1.1" 301 - "-" "Apache-HttpClient/4.5.2 (Java/1.8.0_151)"
119.45.240.155 www.domain.org - [02/Aug/2021:17:04:17 -0500] "POST /xmlrpc.php HTTP/1.1" 301 - "-" "Apache-HttpClient/4.5.2 (Java/1.8.0_151)"
119.45.240.155 www.domain.org - [02/Aug/2021:17:04:49 -0500] "POST /xmlrpc.php HTTP/1.1" 301 - "-" "Apache-HttpClient/4.5.2 (Java/1.8.0_151)"
119.45.240.155 www.domain.org - [02/Aug/2021:17:04:53 -0500] "POST /xmlrpc.php HTTP/1.1" 301 - "-" "Apache-HttpClient/4.5.2 (Java/1.8.0_151)"
119.45.240.155 www.domain.org - [02/Aug/2021:17:05:16 -0500] "POST /xmlrpc.php HTTP/1.1" 301 - "-" "Apache-HttpClient/4.5.2 (Java/1.8.0_151)"
119.45.240.155 www.domain.org - [02/Aug/2021:17:05:26 -0500] "POST /xmlrpc.php HTTP/1.1" 301 - "-" "Apache-HttpClient/4.5.2 (Java/1.8.0_151)"
119.45.240.155 www.domain.org - [02/Aug/2021:17:05:26 -0500] "POST /xmlrpc.php HTTP/1.1" 301 - "-" "Apache-HttpClient/4.5.2 (Java/1.8.0_151)"
119.45.240.155 www.domain.org - [02/Aug/2021:17:05:55 -0500] "POST /xmlrpc.php HTTP/1.1" 301 - "-" "Apache-HttpClient/4.5.2 (Java/1.8.0_151)"
119.45.240.155 www.domain.org - [02/Aug/2021:17:05:57 -0500] "POST /xmlrpc.php HTTP/1.1" 301 - "-" "Apache-HttpClient/4.5.2 (Java/1.8.0_151)"
119.45.240.155 www.domain.org - [02/Aug/2021:17:05:58 -0500] "POST /xmlrpc.php HTTP/1.1" 301 - "-" "Apache-HttpClient/4.5.2 (Java/1.8.0_151)"
119.45.240.155 www.domain.org - [02/Aug/2021:17:05:58 -0500] "POST /xmlrpc.php HTTP/1.1" 301 - "-" "Apache-HttpClient/4.5.2 (Java/1.8.0_151)"
119.45.240.155 www.domain.org - [02/Aug/2021:17:06:08 -0500] "POST /xmlrpc.php HTTP/1.1" 301 - "-" "Apache-HttpClient/4.5.2 (Java/1.8.0_151)"
119.45.240.155 www.domain.org - [02/Aug/2021:17:06:24 -0500] "POST /xmlrpc.php HTTP/1.1" 301 - "-" "Apache-HttpClient/4.5.2 (Java/1.8.0_151)"
Here are the f2b logs for this IP:
2021-08-02 16:43:13,279 fail2ban.filter [791518]: INFO [recidive] Found 119.45.240.155 - 2021-08-02 16:43:13
2021-08-02 16:44:13,185 fail2ban.actions [791518]: NOTICE [evasive] Unban 119.45.240.155
2021-08-02 16:44:13,529 fail2ban.actions [791518]: NOTICE [recidive] Unban 119.45.240.155
2021-08-02 16:44:15,583 fail2ban.actions [794198]: NOTICE [evasive] Restore Ban 119.45.240.155
2021-08-02 16:44:17,590 fail2ban.actions [794198]: NOTICE [recidive] Restore Ban 119.45.240.155
2021-08-02 16:45:12,300 fail2ban.actions [794198]: NOTICE [evasive] Unban 119.45.240.155
2021-08-02 16:45:13,019 fail2ban.filter [794198]: INFO [evasive] Found 119.45.240.155 - 2021-08-02 16:45:12
2021-08-02 16:45:13,511 fail2ban.actions [794198]: NOTICE [evasive] Ban 119.45.240.155
2021-08-02 16:45:13,517 fail2ban.filter [794198]: INFO [recidive] Found 119.45.240.155 - 2021-08-02 16:45:13
2021-08-02 16:46:35,452 fail2ban.filter [794198]: INFO [evasive] Found 119.45.240.155 - 2021-08-02 16:46:34
2021-08-02 16:46:35,635 fail2ban.actions [794198]: WARNING [evasive] 119.45.240.155 already banned
2021-08-02 16:48:34,387 fail2ban.actions [794198]: NOTICE [evasive] Unban 119.45.240.155
2021-08-02 16:50:06,229 fail2ban.filter [794198]: INFO [evasive] Found 119.45.240.155 - 2021-08-02 16:50:05
2021-08-02 16:50:06,317 fail2ban.actions [794198]: NOTICE [evasive] Ban 119.45.240.155
2021-08-02 16:50:06,340 fail2ban.filter [794198]: INFO [recidive] Found 119.45.240.155 - 2021-08-02 16:50:06
2021-08-02 16:51:41,881 fail2ban.filter [794198]: INFO [evasive] Found 119.45.240.155 - 2021-08-02 16:51:41
2021-08-02 16:51:42,283 fail2ban.actions [794198]: WARNING [evasive] 119.45.240.155 already banned
2021-08-02 16:53:00,229 fail2ban.filter [794198]: INFO [evasive] Found 119.45.240.155 - 2021-08-02 16:52:59
2021-08-02 16:53:00,782 fail2ban.actions [794198]: WARNING [evasive] 119.45.240.155 already banned
2021-08-02 16:53:26,979 fail2ban.filter [794198]: INFO [evasive] Found 119.45.240.155 - 2021-08-02 16:53:26
2021-08-02 16:53:27,018 fail2ban.actions [794198]: WARNING [evasive] 119.45.240.155 already banned
2021-08-02 16:55:17,296 fail2ban.filter [794198]: INFO [evasive] Found 119.45.240.155 - 2021-08-02 16:55:16
2021-08-02 16:55:17,577 fail2ban.actions [794198]: WARNING [evasive] 119.45.240.155 already banned
2021-08-02 16:56:49,366 fail2ban.filter [794198]: INFO [evasive] Found 119.45.240.155 - 2021-08-02 16:56:48
2021-08-02 16:56:49,919 fail2ban.actions [794198]: WARNING [evasive] 119.45.240.155 already banned
2021-08-02 16:58:48,269 fail2ban.actions [794198]: NOTICE [evasive] Unban 119.45.240.155
2021-08-02 17:00:09,489 fail2ban.filter [794198]: INFO [evasive] Found 119.45.240.155 - 2021-08-02 17:00:08
2021-08-02 17:00:09,582 fail2ban.actions [794198]: NOTICE [evasive] Ban 119.45.240.155
2021-08-02 17:00:09,589 fail2ban.filter [794198]: INFO [recidive] Found 119.45.240.155 - 2021-08-02 17:00:09
2021-08-02 17:02:08,346 fail2ban.actions [794198]: NOTICE [evasive] Unban 119.45.240.155
2021-08-02 17:02:11,387 fail2ban.filter [794198]: INFO [evasive] Found 119.45.240.155 - 2021-08-02 17:02:10
2021-08-02 17:02:11,559 fail2ban.actions [794198]: NOTICE [evasive] Ban 119.45.240.155
2021-08-02 17:02:11,564 fail2ban.filter [794198]: INFO [recidive] Found 119.45.240.155 - 2021-08-02 17:02:11
2021-08-02 17:04:10,334 fail2ban.actions [794198]: NOTICE [evasive] Unban 119.45.240.155
2021-08-02 17:05:23,151 fail2ban.filter [794198]: INFO [evasive] Found 119.45.240.155 - 2021-08-02 17:05:22
2021-08-02 17:05:23,648 fail2ban.actions [794198]: NOTICE [evasive] Ban 119.45.240.155
2021-08-02 17:05:23,653 fail2ban.filter [794198]: INFO [recidive] Found 119.45.240.155 - 2021-08-02 17:05:23
2021-08-02 17:05:23,761 fail2ban.actions [794198]: WARNING [recidive] 119.45.240.155 already banned
2021-08-02 17:07:22,019 fail2ban.actions [794198]: NOTICE [evasive] Unban 119.45.240.155
2021-08-02 17:09:47,156 fail2ban.filter [794198]: INFO [evasive] Found 119.45.240.155 - 2021-08-02 17:09:46
2021-08-02 17:09:47,412 fail2ban.actions [794198]: NOTICE [evasive] Ban 119.45.240.155
2021-08-02 17:09:47,417 fail2ban.filter [794198]: INFO [recidive] Found 119.45.240.155 - 2021-08-02 17:09:47
2021-08-02 17:10:07,934 fail2ban.filter [794198]: INFO [evasive] Found 119.45.240.155 - 2021-08-02 17:10:07
2021-08-02 17:10:08,053 fail2ban.actions [794198]: NOTICE [evasive] 119.45.240.155 already banned
2021-08-02 17:12:07,207 fail2ban.actions [794198]: NOTICE [evasive] Unban 119.45.240.155
2021-08-02 17:12:34,229 fail2ban.filter [794198]: INFO [evasive] Found 119.45.240.155 - 2021-08-02 17:12:33
2021-08-02 17:12:34,452 fail2ban.actions [794198]: NOTICE [evasive] Ban 119.45.240.155
2021-08-02 17:12:34,457 fail2ban.filter [794198]: INFO [recidive] Found 119.45.240.155 - 2021-08-02 17:12:34
2021-08-02 17:13:03,361 fail2ban.filter [794198]: INFO [evasive] Found 119.45.240.155 - 2021-08-02 17:13:02
2021-08-02 17:13:03,801 fail2ban.actions [794198]: NOTICE [evasive] 119.45.240.155 already banned
2021-08-02 17:15:02,150 fail2ban.actions [794198]: NOTICE [evasive] Unban 119.45.240.155